Hardware-Trusted Security: The Next Frontier in Server Protection
You've probably invested heavily in firewalls, intrusion detection systems, and advanced encryption. Your software security stack looks impressive on paper. But what if I told you there's a vulnerability in your security strategy that you can't patch with software updates? A threat that lives deeper than your operating system, hidden in the very hardware you rely on.
I recently consulted with a financial institution that had all the right software security measures. Their cybersecurity team was top-notch, their protocols were impeccable. Yet they fell victim to a sophisticated attack that originated not from malicious code, but from compromised firmware. The attackers didn't break through their firewalls - they walked right past them through a door that wasn't even supposed to exist.
This isn't science fiction. It's the new reality of server security, and it's why hardware-trusted security is no longer a luxury but a necessity.
The Foundation: Understanding Hardware Roots of Trust
Think of your server's security like a house. Your software security measures are the locks on the doors, the alarm system, the security cameras. But what if someone could tamper with the foundation itself? What if the blueprints could be altered before the house was even built?
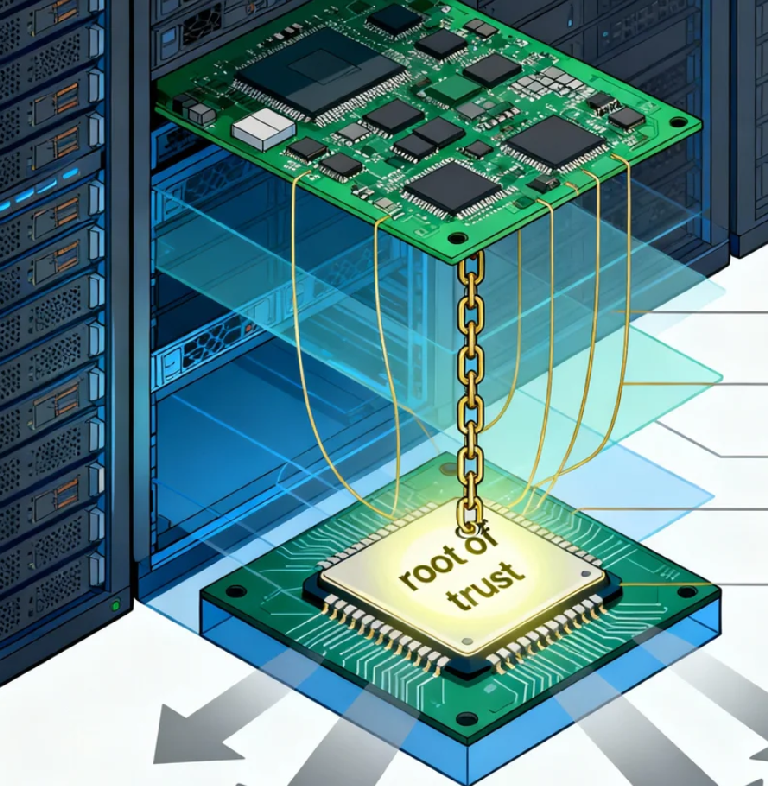
A hardware root of trust is that unchangeable foundation. It's a secure cryptoprocessor embedded in your server hardware that serves as the absolute starting point for everything that follows. Unlike software, which can be modified and manipulated, this hardware anchor provides a fixed reference point that can vouch for the integrity of every subsequent component in your system.
When your server boots up, the hardware root of trust verifies the firmware. The verified firmware then checks the bootloader, which authenticates the operating system, which then validates the applications. This creates a "chain of trust" where each layer can only run if the layer below it proves it's genuine and untampered.
The Invisible Threat: Why Software Alone Isn't Enough
Most organizations operate under the assumption that their hardware is trustworthy. But consider what happens before your server even reaches your data center. During manufacturing, shipping, storage, or even through sophisticated supply chain attacks, hardware and firmware can be compromised in ways that software security will never detect.
I've seen servers with modified BIOS that created hidden backdoors. I've encountered network cards with firmware that secretly copied traffic to external destinations. These aren't theoretical threats - they're happening right now, and traditional security tools are blind to them.
The scary part? You could have the best cybersecurity team in the world, and they'd never know if your server's firmware has been compromised. The malware lives below the operating system, in a realm where conventional security tools simply can't reach.
Practical Implementation: Building Your Hardware Trust Chain
Implementing hardware-trusted security doesn't require replacing your entire infrastructure. It's about strategically implementing verification at critical points in your system.
Start with secure boot. This isn't just about enabling a setting in your BIOS. True secure boot uses cryptographic signatures to verify that each component of your boot process - from firmware to operating system - hasn't been altered. When properly configured, it prevents unauthorized code from running at the most privileged levels of your system.
But don't stop there. Look into trusted platform modules (TPM) and their more modern counterparts. These dedicated microcontrollers perform cryptographic operations and store sensitive data in ways that even the server's main processors can't access directly. They're like having a secure vault built into your server's architecture.
One of our clients, a healthcare provider, implemented TPM-based full disk encryption. Even if someone physically stole their servers, the data remained protected. More importantly, the TPM ensured that the servers would only boot with authorized, untampered software, preventing attackers from bypassing encryption through software manipulation.
Measured Boot: The Security Camera You Never Knew You Needed
Imagine having a security camera that records every single step of your server's startup process. That's essentially what measured boot does. Instead of just verifying components, it cryptographically records measurements of each boot component into the TPM.
This creates an unforgeable audit trail of everything that happened during startup. If something goes wrong - or if you just want to verify everything is as it should be - you can review these measurements to identify exactly where any anomalies occurred.
I helped an e-commerce company implement measured boot after they experienced mysterious performance issues. The measurements revealed that a compromised driver was loading during boot, something their security software had completely missed. They replaced the driver, and the issues vanished.
The Future Is Already Here: Hardware Security in Practice
The beauty of hardware-trusted security is that once implemented, it works silently in the background. You don't need to manage it daily. It becomes part of your infrastructure's DNA, providing continuous protection even when you're not actively thinking about it.
Start with an assessment of your current hardware capabilities. Many modern servers already have TPMs or similar technology - they're just not configured or used effectively. Work with your hardware vendors to understand what security features your existing equipment supports.
Then, develop a phased implementation plan. Begin with your most critical systems - the ones handling sensitive data or essential services. Configure secure boot, enable TPM functionality, and establish proper key management procedures.
Remember, hardware-trusted security isn't about replacing your existing security measures. It's about adding a deeper layer of protection that addresses threats your software security can't even see. In today's threat landscape, that depth might be what separates a minor security incident from a catastrophic breach.
+

