The Zero-Trust CDN: Embedding Security into Every Layer of Content Delivery
Remember when we used to build castles? We'd put up strong walls around our network, create a single heavily guarded gateway, and assume everyone inside was trustworthy. That was the old "trust but verify" model for CDN security. But in today's world of sophisticated attacks and distributed workforces, those castle walls are useless. The threat isn't just outside the walls - it's already inside, or the attackers have learned to look exactly like legitimate visitors.
I was reviewing security logs with a client last week when we discovered something chilling. Their traditional CDN was faithfully serving malicious bots the same way it served legitimate users - because from its perspective, both looked identical. The CDN was doing its job of accelerating content, but it was accelerating threats right along with legitimate traffic. That's when the CTO turned to me and said, "We're not just distributing content anymore - we're distributing risk."
The Fundamental Shift: From Perimeter to Persistent Verification
Traditional CDN security operates like a nightclub bouncer checking IDs at the door. Once you're in, you can move anywhere. Zero-Trust CDN is more like a top-level security detail that never stops verifying your identity, never assumes you belong anywhere, and constantly monitors your behavior.
The core principle is brutal in its simplicity: never trust, always verify. Every request - whether for a product image, API response, or video stream - gets treated as potentially hostile until proven otherwise. And this verification doesn't happen just once at the "gate." It happens at every layer, for every request, regardless of where it's coming from.
Identity-Aware Edge: The New First Line of Defense
Imagine if your CDN edge nodes could do more than just check for valid TLS certificates. What if they could understand who is making each request, what they're allowed to access, and whether their behavior matches normal patterns?
We implemented this for a financial services client who was struggling with credential stuffing attacks. Their traditional CDN saw these as legitimate login attempts - after all, they were using valid user credentials. But with identity-aware edges, we could detect that these requests were coming from unfamiliar locations, using suspicious user agents, and exhibiting timing patterns that didn't match human behavior.
The result? They blocked 98% of credential stuffing attempts before those requests ever reached their origin servers. More importantly, legitimate users experienced zero additional friction because the system learned their normal behavior patterns.
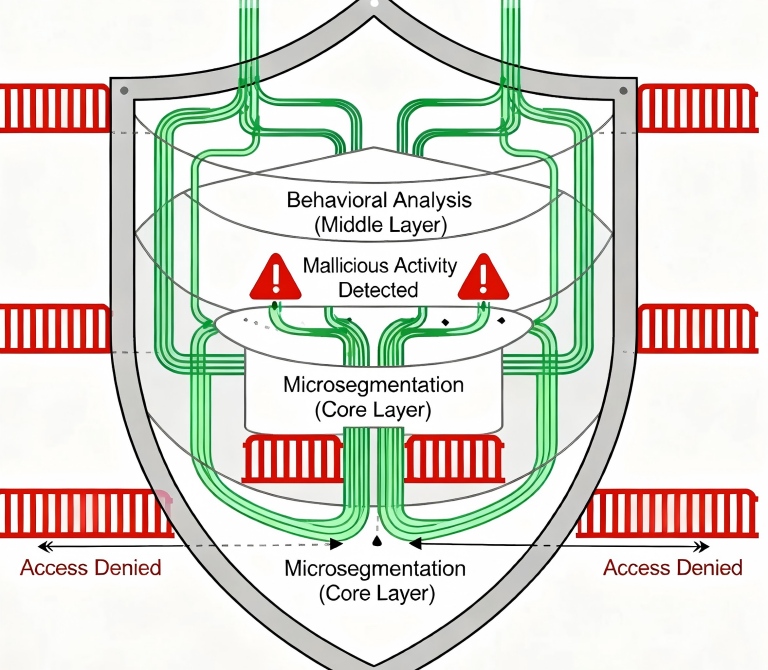
Microsegmentation at the Edge: Containing the Blast Radius
In a Zero-Trust CDN architecture, every piece of content exists in its own security domain. Even if an attacker compromises one asset, they can't use it as a springboard to access others.
Think of it like a modern office building where each room has its own keycard access. Just because you can enter the lobby doesn't mean you can access the server room. Similarly, in a Zero-Trust CDN, accessing a public product image doesn't grant you any privileges to reach customer data or admin interfaces.
I helped an e-commerce platform implement this after they suffered a data breach that started with a compromised product image. The attacker used a vulnerability in their image processing pipeline to jump laterally to their customer database. With microsegmentation, even if they compromise one component, the attack can't spread beyond its immediate environment.
Continuous Threat Assessment: The CDN That Never Sleeps
Traditional security models check credentials once and then create a session. Zero-Trust CDN continuously monitors for threat indicators throughout the entire delivery chain.
One of our most effective implementations uses real-time threat intelligence to score every request based on hundreds of behavioral indicators. A user might start a session looking completely legitimate, but if they suddenly start making requests at an inhuman pace or accessing resources in an unusual sequence, their threat score increases and they're challenged for additional verification.
This approach caught a sophisticated attack against a media company where attackers slowly built up "legitimate" looking traffic over several hours before launching their actual attack. The Zero-Trust CDN detected the subtle shift in patterns and automatically escalated security measures before any damage occurred.
Encryption Everywhere: No More Plaintext Weaknesses
Many organizations make the mistake of thinking HTTPS to the edge is sufficient. But in a Zero-Trust model, we encrypt everything - between edge nodes, between data centers, even between different services within the same facility.
I recall a retail client who discovered their internal CDN analytics were being intercepted because they'd assumed their internal network was "trusted." In a Zero-Trust CDN, there are no trusted networks - only encrypted communications between verified endpoints.
Practical Implementation: Making Zero-Trust Work Without Breaking Everything
The biggest fear I hear from clients is that Zero-Trust will mean constant authentication challenges for legitimate users. But the reality is quite the opposite when implemented correctly.
Start with your crown jewels. Identify your most sensitive content and APIs, and apply Zero-Trust principles there first. For most organizations, this means customer data, admin interfaces, and proprietary content.
Next, implement gradually. We typically start with monitoring mode, where we score requests and log potential threats without taking action. This gives us a baseline and helps tune our policies before we start blocking anything.
Finally, make it invisible to legitimate users. Through machine learning and behavioral analysis, you can create "trust profiles" that allow regular users to move seamlessly while still challenging suspicious activity.
The transition to Zero-Trust CDN isn't about adding more security layers - it's about fundamentally rethinking how security integrates with content delivery. It's recognizing that in today's threat landscape, the question isn't if you'll be targeted, but when. And when that happens, you want a content delivery network that's not just fast, but also inherently secure by design.

