From Certificates to Mesh: A Guide to Building a Verifiable Global Service Architecture on SSL
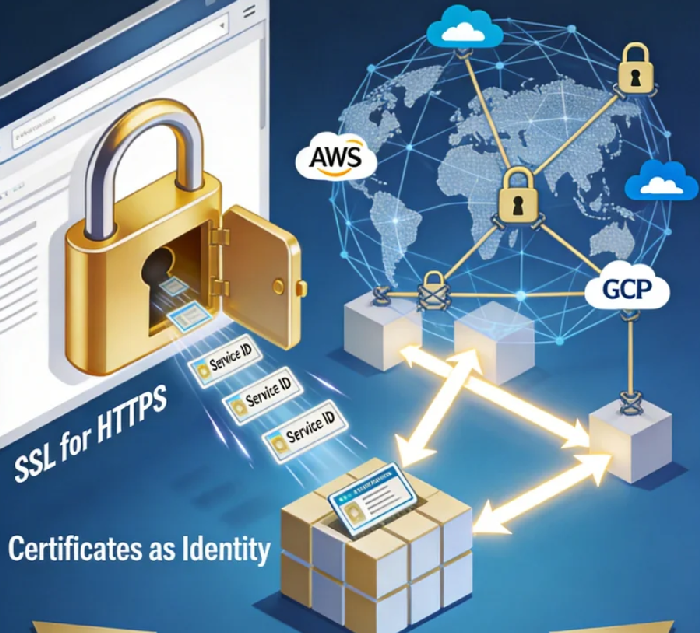
Let's be honest about that padlock icon. For years, we've treated the SSL/TLS certificate as a checkbox—a necessity for the green bar or to stop browsers from screaming. It’s been filed under "compliance" or "basic web hygiene." But what if I told you that this humble piece of cryptographic data, sitting in your server's directory, is the single most underutilized key to unlocking a secure, resilient, and truly verifiable global architecture?
We're at an inflection point. The old model of security—building a hard shell (firewall) around a soft, trusted interior—is not just outdated; it's dangerously obsolete. In a world where your application might span three cloud providers, a private data center in Frankfurt, and edge nodes in São Paulo and Singapore, the very concept of a "network perimeter" evaporates. Your payment service in AWS us-east-1 needs to talk to your user database in Google Cloud's europe-west1, and both must trust a logistics API running on-premises. How do they know who's who?
The answer has been hiding in plain sight. The same technology that lets a browser trust https://yourbank.com can be architecturally repurposed to let your services trust each other. This is the journey from certificates to mesh: evolving SSL from a tool for encrypting human traffic into the foundational identity layer for all machine-to-machine communication in a zero-trust world.
Part 1: The Perimeter is Dead. Identity is the New Firewall.
The shift begins with a sobering admission: your greatest threat is no longer the external attacker, but the authenticated impostor inside. Once someone (or some thing) is inside your network boundary, traditional security models offer little resistance. A compromised microservice can run amok.
This is the core dilemma of distributed systems. When every service instance is ephemeral, scaling up and down across global zones, IP addresses become meaningless identifiers. You can't write a firewall rule that says "allow 10.0.5.12" when that pod might live for only 5 minutes. The only constant, verifiable attribute a service possesses is its cryptographic identity—its certificate.
Here’s the counterintuitive leap: Stop securing the network. Start securing the conversation. Instead of trying to control which machines can talk (a losing battle in dynamic environments), enforce that any conversation must be between strongly identified parties. This is the essence of mutual TLS (mTLS), where both client and server present and validate certificates, not just the server. It turns every TCP connection into a securely introduced handshake.
Part 2: Laying the Foundation: Your Certificate Authority as the Root of Trust
To build this, you need a source of truth for identity—a Certificate Authority (CA) that your entire architecture trusts. This isn't necessarily a public CA like DigiCert (though they play a role for external faces). This is your private, internal root of trust.
Think of it as your company's digital passport office. Every service, from your monolithic legacy app to your newest serverless function, gets a digital "passport" (a certificate) issued by this authority. When two services communicate, they check each other's passports. If they're both issued by the same trusted authority, they can proceed. This creates a cryptographic mesh of trust, completely decoupled from the underlying network topology.
The critical technical shift here is moving from long-lived, manually provisioned certificates to short-lived, automatically rotated certificates. A certificate valid for 90 days is a liability; one valid for 24 hours is a manageable credential. This is where tools like HashiCorp Vault or cert-manager (for Kubernetes) become architectural linchpins. They automate the issuance and renewal of these service identities, a task that is impossible at scale for humans.
HashiCorp Vault: https://www.vaultproject.io/
cert-manager: https://cert-manager.io/
Part 3: The Service Mesh: The Nervous System for Your Certificate Identity
Now, having certificates is one thing. Enforcing mTLS and identity-aware policies across hundreds of services in real-time is another. This is where the service mesh enters the stage—not as another piece of infrastructure, but as the essential runtime enforcer of your certificate-based identity system.
A service mesh like Istio or Linkerd operates as a decentralized infrastructure layer. It injects a lightweight proxy (sidecar) next to each service instance. This proxy is the workhorse of our architecture:
It automatically obtains a unique certificate (from Vault, cert-manager, etc.) for its service.
It intercepts all inbound and outbound traffic.
For every outbound request, it performs a mTLS handshake with the destination's proxy, verifying certificates.
It also enforces fine-grained policies: "Is Service A allowed to call the
POST /transactionendpoint of Service B?" based on their identities, not IPs.
The mesh provides the critical operational capabilities: observability (who is talking to whom?), reliability (retries, timeouts), and most importantly, transparent security. Developers write business logic; the mesh handles the secure communication, using the certificates you've provisioned as the source of identity.
Istio: https://istio.io/
Linkerd: https://linkerd.io/
Part 4: The Global Verifiable Architecture: Pieces in Concert
So, what does this look like at a global scale? Imagine your three-tiered architecture:
Tier 1: The Root of Trust. A highly secure, globally accessible private CA. This is your crown jewel, kept offline or in the most secure enclave.
Tier 2: The Issuance & Policy Layer. Vault or a cloud-based CA service (like AWS ACM Private CA, GCP Certificate Authority Service). These intermediate CAs, signed by your root, issue the short-lived certificates. This is also where you define high-level policy.
Tier 3: The Runtime Enforcements. The service mesh proxies in every cluster across every region. They hold the certificates, perform mTLS, and report telemetry.
A user request from Tokyo hits your CDN, which has its own certificate. The CDN forwards the request to your API gateway in asia-northeast1. The gateway's mesh proxy verifies the CDN's cert and then makes a call to the user service in europe-west1. Another mTLS handshake occurs across the ocean, verified by the same root trust chain. The entire path is encrypted and every hop is authenticated. You have a verifiable audit trail of service identity at every step.
Part 5: The Unexpected ROI: Beyond Security
The narrative here is often security-first, but the strategic ROI extends far beyond. When every service has a verifiable identity:
Debugging becomes surgical. You can trace a request through a maze of services with absolute certainty about which service instances were involved.
Compliance is demonstrable. For regulations like GDPR or financial standards, you can prove access controls and data flow between named entities, not vague network segments.
Mergers & Acquisitions become smoother. Integrating two companies' systems becomes a matter of cross-signing CAs or establishing federated trust, not a nightmare of network rewiring.
The most compelling data point? Companies that implement this identity-first, zero-trust model report a dramatic reduction in "incident blast radius." A misconfigured or compromised service can't simply connect to anything else. It's contained by its identity, limiting potential damage.
Conclusion: Building Your Trust Fabric
The journey from seeing certificates as a web server cost to treating them as the fabric of service identity is a profound architectural mindset shift. It moves security from being a perimeter-based, network-team concern to an intrinsic property of the application platform itself.
You don't need to boil the ocean. Start by establishing your internal CA. Begin issuing certificates for your most critical services. Experiment with a service mesh in a non-critical environment. The goal is to start weaving this trust fabric—one verifiable connection at a time.
In the end, the most resilient systems aren't those with the hardest shells, but those with the strongest bonds of verified trust between their components. Your SSL certificates are the thread. It's time to start weaving.

