From Manual Renewal to Autopilot: How AI Reshapes Cost and Risk Control for SSL & Global Infrastructure
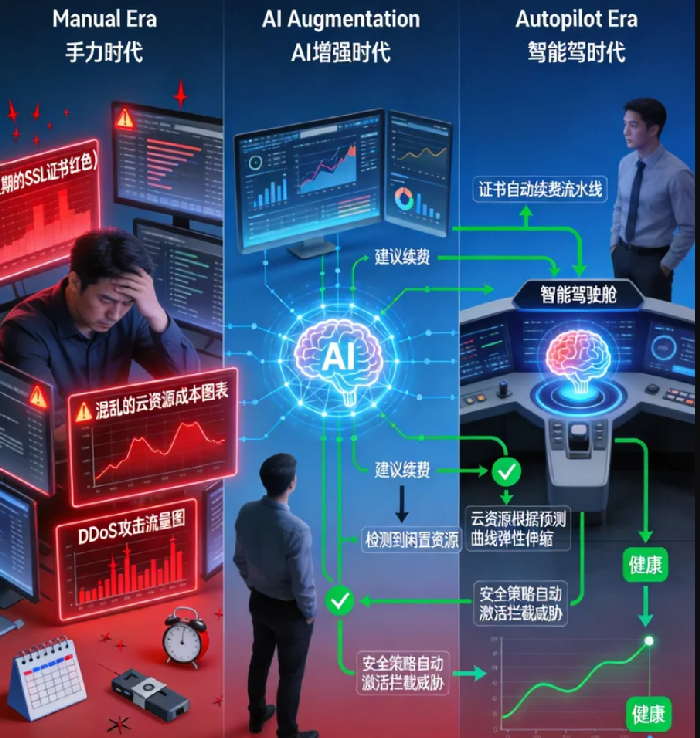
Let's be brutally honest for a moment. That monthly ritual of checking SSL certificate dashboards, the quarterly shock of an unpredictable cloud bill, and the 3 a.m. alert about a regional traffic spike—these aren't just operational chores. They're symptoms of a fundamental mismatch. We're trying to manage dynamic, global, interconnected 21st-century digital infrastructure with static, manual, 20th-century mental models and tools. It's like using a paper map and a compass to fly a jetliner.
The result? A staggering 30% of enterprises experience at least one major service disruption annually due to an unexpected SSL/TLS certificate expiration, despite most certificates providing a 90-day renewal window. On the cloud cost side, a persistent "silent tax" drains budgets: industry analyses consistently show that 25-35% of cloud spend is wasted on over-provisioned or idle resources. The problem isn't a lack of effort; it's a limit of human-scale cognition in a hyper-scale environment.
This is where the paradigm must flip. We're on the cusp of shifting from manual driving—where human operators react to dashboard warnings—to infrastructure autopilot. In this new paradigm, artificial intelligence doesn't just assist; it proactively perceives, predicts, and prescribes, transforming cost and risk from constant battles into managed outcomes. Let's explore what it truly means to put your SSL estate and global infrastructure on autopilot.
Part 1: The Pillars of the Autopilot: Beyond Simple Automation
First, let's demystify the "autopilot" analogy. True autopilot in aviation isn't a single switch; it's a layered system of sensors, predictive models, and control systems working in concert. Similarly, AI-driven infrastructure management is built on three core pillars:
1. Unified Observability & Correlation: The autopilot needs a complete sensory picture. This means ingesting and correlating data that's traditionally siloed: SSL certificate metadata (issuer, expiry, SANs), cloud resource utilization (CPU, memory, network egress), CDN traffic patterns, application performance metrics (latency, error rates), and even external threat intelligence feeds. An AI can then see that a spike in TLS handshake errors in Tokyo is coinciding with a cost spike for a specific Compute Optimized instance family in us-east-1—a connection no human analyst would likely make.
2. Predictive Pattern Recognition & Forecasting: Here’s where we move from reactive to proactive. Machine learning models analyze historical and real-time data to identify patterns. They can forecast with high accuracy:
The precise date a certificate will be at risk of expiration based on team deployment velocity and past renewal lag times.
Next week's traffic load for your e-commerce site in Frankfurt, accounting for seasonality, a planned marketing campaign, and even local weather forecasts.
The likelihood of a DDoS attack based on anomalous port scanning activity observed at your edge nodes.
3. Prescriptive, Closed-Loop Automation: This is the "control system." It doesn't just alert ("Certificate expiring soon!"); it prescribes and executes the optimal action within defined guardrails. For example:
For SSL: It initiates the renewal for a business-critical EV certificate 45 days out, validates it against current CA/B Forum rules, deploys it to staging for a canary test, and then rolls it out to production load balancers and CDN configurations during a low-traffic window—all with a full audit trail.
For Infrastructure: It identifies a cluster of underutilized
c5.4xlargeinstances running a batch job, calculates that switching to Spot Instances with a fallback tom5.4xlargewould save 68% with minimal risk, and executes the change after notifying the resource owner.
This system is embodied in the practice of AIOps (Artificial Intelligence for IT Operations). Think of tools like HashiCorp Vault for secrets and certificate lifecycle, integrated with the policy-driven automation of AWS Certificate Manager (ACM) or Google Cloud's Certificate Authority Service, all fed by the observability stacks of Datadog or New Relic.
Part 2: The SSL Certificate Revolution: From Calendar Alerts to Risk Profiles
Managing certificates today is largely a game of calendar management. The autopilot approach transforms each certificate from a simple expiry date into a dynamic Risk Profile.
A traditional view: *"Certificate for api.payments.example.com expires on 2025-10-15."*
An AI-driven Risk Profile evaluates:
Expiry Risk Score: High. This protects the core payments API. Historical data shows the finance team's deployments are complex, averaging 7-day lead times.
Security Posture Score: Medium. It uses TLS 1.3, but its cryptographic cipher suite is flagged for a planned deprecation in 9 months.
Business Impact Score: Critical. An outage would halt all transactions, estimated at $12,000 per minute.
Dependency Map: This certificate is linked to 3 CDN configurations, 2 API gateway pools, and a legacy on-premises load balancer.
With this profile, the autopilot doesn't just set a reminder. It:
Prioritizes: This certificate jumps to the top of the renewal queue.
Orchestrates: It creates a phased rollout plan, updating the CDN (via Terraform) first, then the cloud gateways, finally coordinating a maintenance window for the on-prem hardware.
Validates Continuously: Post-renewal, it doesn't just check for a valid chain. It actively probes the endpoints from global points of presence to ensure the new certificate is serving correctly and not causing increased handshake latency.
The outcome? The "30% failure rate" becomes a near-zero statistic. Risk is managed not by frantic human intervention, but by systematic, intelligent orchestration.
Part 3: Global Resource Optimization: The End of Static Provisioning
The second frontier is cost. The cloud's promise of elasticity is often betrayed by static, "set-and-forget" provisioning. Autopilot introduces dynamic, continuous optimization.
Consider a global video streaming service. Traffic peaks in Europe during evening hours, shifts to North America, then to Asia. A human team might provision for the global peak everywhere, wasting millions. The autopilot model treats this as a continuous optimization problem:
It predicts the load for each region 2 hours ahead using unique regional models.
It computes the most cost-effective way to meet that load: Should it scale up auto-scaling groups in
eu-west-1, or leverage excess capacity ineu-central-1and use cost-optimized inter-AZ traffic? It factors in the real-time price of Spot Instances, Reserved Instance coverage, and even the cost of data transfer between services (which can be impacted by TLS termination points).It executes and learns the decision, measuring the actual versus predicted cost and performance, refining the model for next time.
This is where tools like AWS Cost Explorer's anomaly detection or Google Cloud's Recommender APIs provide the foundational data. The autopilot system consumes these recommendations, enriches them with application-aware context (e.g., "this instance is part of the stateful database cluster, not the stateless web tier"), and safely executes the savings.
The result is the eradication of the "silent tax." Costs become a predictable, optimized output of the system, not a volatile input to be constantly fought.
Part 4: The Conjoined Twins: Security and Performance Autonomy
The most profound shift occurs when the autopilot manages the intrinsic tension between security and performance. Traditionally, this is a manual trade-off: "We need stronger encryption, even if it's slower."
An AI-driven system manages this autonomously. It operates on a Policy Plane defined by architects (e.g., "Financial data must always use FIPS-validated modules and TLS 1.3; public media content should optimize for 95th-percentile latency").
For a user streaming a movie, the system might select a lighter, faster cipher suite at a nearby edge location, optimizing for speed.
The moment that same user clicks "Upgrade to Premium," their session is seamlessly transferred, and subsequent API calls to the billing service are automatically secured with the strongest available enterprise-grade TLS, with the system accepting the minimal latency penalty as a cost of security.
If a zero-day vulnerability in a common TLS library (like Heartbleed or LOGJAM) is disclosed, the autopilot can immediately assess exposure across the entire global infrastructure, pinpoint vulnerable endpoints, and orchestrate a patching or cipher suite rotation rollout prioritized by asset criticality, often before a human team has finished reading the CVE advisory.
This is the pinnacle of autopilot: a self-defending, self-optimizing system that makes nuanced, context-aware decisions in real-time, at a scale and speed impossible for humans.
Conclusion: The Destination is Not Hands-Free, but Mind-Free
The goal of infrastructure autopilot is not to eliminate the human role, but to elevate it. It's about freeing engineering talent from the tedium of renewal calendars, cost anomaly hunts, and reactive security patching. It shifts their focus from operating the infrastructure to defining its intent—setting the policies, goals, and guardrails within which the AI operates.
We are moving from an era where value is drained by silent costs and punctuated by operational risks to one where cost and risk are compressed outputs of an intelligent, autonomous system. The question is no longer if AI will reshape this landscape, but how quickly you can transition from being a manual driver, eyes glued to a hundred dashboards, to becoming the architect of your own autopilot. The controls are here. It's time to engage them.

