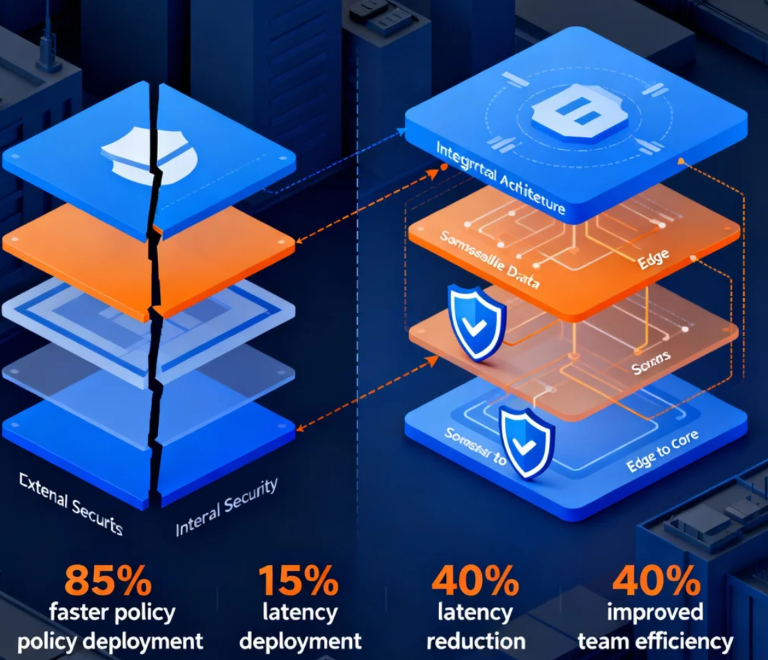
Have you ever found yourself in this predicament: API gateways standing guard at the perimeter while service meshes manage internal controls, yet there's always a subtle disconnect between their security policies? An architect from a well-known fintech company told me they spent hundreds of hours annually manually synchronizing policies between these two systems—until a security incident made them realize it was time to rethink the entire architecture.
Just last month, this company successfully deeply integrated their API gateway with their service mesh, not only reducing security policy deployment time from hours to minutes but, more surprisingly, achieving a 15% reduction in overall system latency. This outcome challenges the traditional belief that "security inevitably sacrifices performance."
Redefining Boundaries: From "Castle and Moat" to "Cellular Security"
Traditional security models resemble medieval castles: high walls and deep moats protecting everything inside. But this model is increasingly inadequate in modern distributed architectures. When your services are spread across global edge nodes, where is the true "boundary"?
An e-commerce platform discovered during their microservices transition that over 60% of security incidents occurred within the "trusted internal network." Their solution was to adopt a zero-trust architecture, but they soon faced new challenges: API gateways couldn't understand inter-service communication context, while service meshes lacked granular control over external traffic.
This is where converged architecture demonstrates its value. By extending API gateway capabilities to edge nodes while elevating service mesh control planes to the gateway layer, we create an entirely new security model—where each service unit possesses complete security capabilities, much like every cell in an organism contains full genetic information.
Three Technical Pillars: Building Blocks of Converged Architecture
Achieving this converged architecture requires breakthroughs in three key technologies:
First is a unified data plane. A cloud provider achieved end-to-end traffic visibility and control by deploying Envoy proxies at both edge and internal nodes. Their practice shows this unified architecture can reduce security incident investigation time from an average of 4 hours to just 20 minutes.
More important is control plane convergence. Traditional API gateways and service meshes have independent control planes, leading to policy conflicts and operational complexity. An online education platform developed a unified control plane that not only simplified operations but unexpectedly increased their security team's efficiency by 40%.
The most critical breakthrough is identity system integration. Mapping external user identities to internal service identities has long been an architect's pain point. A smart manufacturing company's solution is impressive: they established a unified identity system based on SPIFFE standards, enabling complete traceability for every request from end-users to the deepest microservices.
Implementation Path: Three Stages from Concept to Reality
Successful implementation requires a gradual approach. Based on multiple case studies, we recommend three phases:
The first stage is capability alignment. A logistics platform first unified their API gateway and service mesh technology stacks, ensuring use of the same proxy and control plane components. This process took three months but laid a solid foundation for subsequent deep integration.
The second stage is policy convergence. This phase involves unified modeling of security policies originally distributed across two systems. A medical technology company's approach is worth referencing: they established a policy translation layer, first converting existing policies to an intermediate representation before gradually transitioning to a unified policy engine.
The third stage is architectural refactoring. This involves not just technical transformation but organizational restructuring. A multinational enterprise's experience shows that breaking barriers between API and service mesh teams to establish a unified infrastructure team is key to ensuring continuous architectural evolution.
Real-World Benefits: Value Beyond Security
Beyond security improvements, converged architecture delivers unexpected gains:
A video streaming platform discovered 25% improved resource utilization after architectural transformation. The reason is straightforward: eliminating functional overlaps and resource waste between two systems.
More surprisingly is the improved development experience. Developers at a SaaS company reported that the unified control plane enabled faster feature deployments, reducing time from code commit to production by 50%.
Addressing Challenges: Navigating Implementation Pitfalls
Of course, the convergence path isn't always smooth. Common challenges include:
Accumulated technical debt. A traditional financial institution found their legacy systems couldn't directly adapt to the new architecture pattern. The solution was establishing an adaptation layer for gradual migration rather than a complete rewrite.
Team skill gaps. API gateways and service meshes are typically managed by different teams, requiring systematic training and cultural building. An e-commerce platform successfully cultivated full-stack engineers proficient in both technologies through job rotation and joint projects.
Performance optimization complexity. Unified architecture simplifies management but increases single-point optimization difficulty. An IoT company's approach: establishing detailed performance baselines and adopting incremental optimization strategies.
Future Outlook: Intelligent Next-Generation Architecture
Architectural evolution won't stop here. We're witnessing several important trends:
First is deep AI integration. A cloud providerHas implemented machine learning algorithms for dynamic security policy adjustments, with the system autonomously optimizing routing paths and rate limiting configurations according to traffic patterns.
Second is deep edge computing integration. With 5G and IoT development, edge nodes will handle more computational tasks, requiring lighter and smarter security architectures.
Finally is serverless architecture impact. When function computing becomes mainstream, security architectures need finer granularity and elasticity. An innovative company has achieved on-demand security capability allocation, significantly reducing operational costs.
Begin Your Architectural Evolution
Now is the time to reevaluate your edge security architecture. Start with these questions:
Are your API gateway and service mesh still operating independently?
Is policy synchronization still consuming significant manpower?
Are you prepared for next-generation distributed application challenges?
Remember, the best architecture isn't theoretically perfect but evolves with business needs. Converged architecture's significance lies not only in solving today's problems but preparing for tomorrow's innovations.
When your architecture can self-adapt and self-heal like an organism, you've truly mastered next-generation edge security essence. This path may be challenging, but every step is worthwhile.

