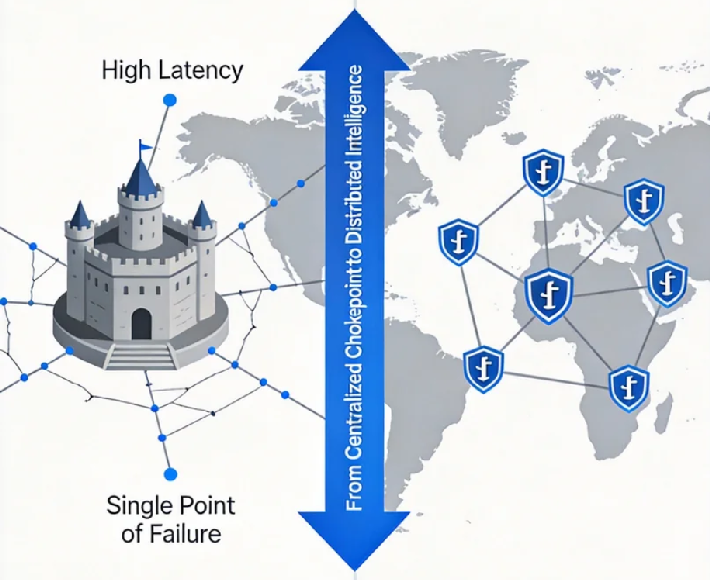
Forget the old map. The one that showed your headquarters at the center, with fragile, straining lines connecting it to the rest of the world. That map is obsolete. In today's digital-first global market, your business doesn't just connect to the world from a single point; it must exist within it, simultaneously and securely, everywhere your customers are. This is no longer about building faster highways to a central castle. It's about constructing a distributed, intelligent, and secure presence—a true Global Footprint.
The journey to build this footprint begins with a fundamental mindset shift: moving from a centralized, perimeter-based security model to an architecture of dispersion. It's about strategically placing your digital assets—not just data caches, but logic, security, and identity—at the edge of the network, as close to the user as possible. This is where the transformative duo of Edge Security and Edge Delivery converges, not as separate tools, but as the integrated foundation of your global strategy.
The Architecture of Dispersion: Why the Center Cannot Hold
For decades, the dominant model was the "hub-and-spoke." All traffic, from Singapore to San Francisco, routed back to your primary data center, where a fortress of firewalls stood guard. This created a single point of failure, introduced crippling latency (the physics of light are unforgiving), and concentrated risk. A DDoS attack didn't need to overwhelm your global business, just that one, overburdened gateway.
The modern alternative is the architecture of dispersion. Think of it as replacing a single, heavily fortified embassy with a network of smart, secure, local consulates in every major city. Each consulate (edge node) can authenticate citizens (users), process routine requests (deliver static and dynamic content), and apply local laws (compliance rules), without always burdening the central government (origin servers).
This shift is powered by the convergence of two evolutionary paths:
From CDN to Intelligent Edge Delivery: What began as simple content caching has evolved into a globally distributed platform capable of running serverless functions, personalizing content in real-time, and optimizing APIs—all at the edge.
From Firewall to Identity-Aware Edge Security: Security has moved from guarding a network perimeter to verifying every single request, regardless of its origin, based on identity and context. This Zero Trust principle is enforced at the edge, the first point of contact.
When you architect with this dispersed model, speed becomes a byproduct of a superior architecture, not the primary goal. The goal is proximity, intelligence, and inherent security.
The Intricate Dance: How Edge Security and Delivery Are Intertwined
To see them as separate is to miss the point. In a dispersed architecture, security and delivery are two sides of the same coin, each making the other more effective.
1. Security as an Enabler of Speed (The Counterintuitive Truth)
Conventional wisdom says security checks slow things down. At the edge, the opposite can be true. Consider a malicious bot attack scraping your product catalog. In the old model, each bot request travels the full network round-trip, consuming origin bandwidth and resources. With security at the edge, malicious traffic is identified and blocked within milliseconds, before it traverses your backbone. This "clean traffic" effect ensures your origin only processes legitimate requests, dramatically improving performance for real users. A robust Web Application Firewall (WAF) and DDoS mitigation at the edge aren't just shields; they are performance optimization tools.
2. Delivery as a Vector for Security Context
Intelligent edge delivery provides the rich data that makes edge security smarter. A global load balancer doesn't just route traffic; it sees global attack patterns in real-time. It can detect a sudden surge of requests from a new region and automatically apply stricter security policies. Furthermore, by managing TLS/SSL termination at the edge, you centralize certificate management, enforce the strongest encryption protocols globally (like TLS 1.3), and eliminate the risk of misconfiguration across multiple origin servers. Your content delivery network becomes your first and most insightful line of defense.
3. The Zero-Trust Edge: Identity is the New Perimeter
This is the core conceptual leap. In a dispersed world, the question shifts from "Are you inside my network?" to "Who are you, and what are you allowed to do?" Every API call, every image request, every login attempt must be verified. This is where technologies like Secure Access Service Edge (SASE) manifest at the edge. By integrating identity-aware proxies and granular policy enforcement into the global edge platform, you can ensure that a user in Berlin only accesses the data they are authorized for, while a partner API in Tokyo is limited to specific endpoints—all without forcing that traffic through a corporate VPN.
Building Blocks: The Pillars of Your Global Footprint
Architecting this footprint requires intentional selection of capabilities. Here are the non-negotiable pillars:
A Globally Distributed, Unified Platform: You need a single pane of glass for both delivery and security policy management. Managing a CDN from one vendor and a WAF from another creates gaps and operational nightmares. The edge platform must be inherently global.
Intelligent, Origin-Shielding Security: DDoS protection, WAF, and bot management must be activated at the edge, with the ability to absorb massive attacks and pass only legitimate traffic to your origin. This protects your infrastructure and reduces cost.
API Acceleration & Security: Modern applications are API-driven. The edge must optimize API response times through intelligent routing and caching of dynamic content, while simultaneously applying rate-limiting, schema validation, and authentication to every API call.
Programmable Edge (Serverless): The ability to run lightweight, secure code at the edge (e.g., Cloudflare Workers, AWS Lambda@Edge) is a game-changer. Use it to personalize content, perform A/B testing, implement custom security logic, or reshape responses for different devices—all without touching your origin.
Holistic Visibility & Analytics: You cannot manage what you cannot measure. The platform must provide unified logs and analytics that correlate security events with performance metrics, answering questions like: "Did that API slow down because of a legitimate traffic spike or a nascent bot attack?"
The Strategic Payoff: More Than Just Technology
Adopting this architecture is a strategic business decision with tangible returns:
Resilience: A distributed footprint is inherently resilient. The failure of one region or even one provider's network has minimal impact on global availability.
Compliance & Data Sovereignty: You can implement fine-grained controls at the edge to ensure data from EU citizens is processed according to GDPR rules, even if your origin is elsewhere. Edge logic can filter, anonymize, or redirect data to comply with local regulations.
Developer Velocity: By offloading common concerns (security, scaling, global distribution) to the edge platform, your development teams can focus on building core application logic, accelerating innovation.
The New Map: Your Business, Living at the Edge
We started by discarding the old map. The new one doesn't have a center. It shows a luminous, interconnected mesh of points of presence—your Global Footprint. At each point, security and delivery work in concert, delivering experiences that are not only fast but also secure, personalized, and compliant by design.
This is not a future state; it's an achievable architecture today. The question is no longer if you need a global edge strategy, but how deliberately you will architect it. Moving beyond speed means embracing an architectural paradigm where your global presence is your greatest asset—intelligent, secure, and inherently resilient. It means building a business that truly lives where your users are.

