Beyond TCP: How HTTP/3 & QUIC Are Redefining the Future of Servers, SSL & CDN Architecture
Let’s be blunt: the finely tuned TCP kernel parameters, the meticulously cached TLS sessions, and the latency-predicting CDN algorithms your team has spent years perfecting are becoming the digital equivalent of a beautifully crafted horse whip—elegant, but fundamentally obsolete in the face of an engine revolution.
A streaming company’s architect discovered a perplexing truth at 3 AM: their mobile users experienced 37% more playback buffering than Wi-Fi users, despite ample bandwidth. The culprit wasn’t their servers, CDN, or codecs. It was a 47-year-old protocol: TCP. Every time a mobile device switched cell towers, TCP’s “three-way handshake” and “slow start” mechanisms forced a reconnection as cumbersome as restarting a steam locomotive.
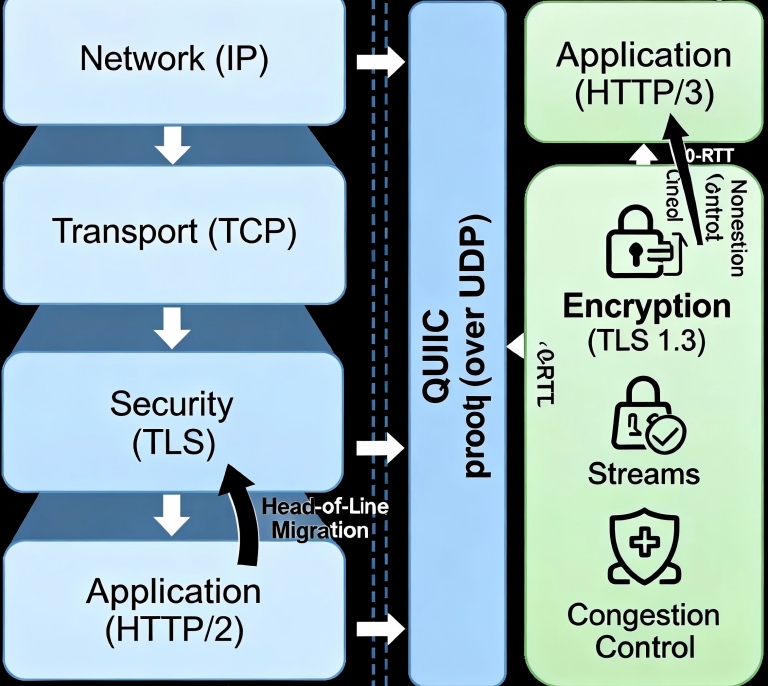
This is the silent earthquake reshaping the internet’s bedrock: HTTP/3 and the QUIC protocol are re-engineering how data flows from the transport layer up. This isn’t a simple version upgrade. It’s a “ground-up” re-excavation of the network stack that will force servers, SSL/TLS, and CDNs to fundamentally reconsider their roles and how they collaborate.
The Mid-Life Crisis of a 47-Year-Old Protocol
We must face TCP’s limitations honestly. Designed in 1974, it assumed networks were stable, wired, and predictable. Today's networks are mobile, wireless, and fragmented. When your phone switches cell towers on a subway, TCP treats each shift as a traumatic "connection death and rebirth."
The more fundamental flaw is Head-of-Line (HOL) Blocking. In HTTP/2, multiple requests share one TCP connection. But if a single packet is lost, the entire connection must pause and wait for retransmission, blocking all other requests. It’s a multi-lane traffic jam caused by one fender-bender.
QUIC’s (Quick UDP Internet Connections) genius is its radical divorce from TCP, rebuilding transport logic atop user-space UDP. This means:
Stream Independence: Packet loss in one stream doesn't block others.
Connection Migration: A device can move from WiFi to 5G without re-handshaking.
0-RTT Resumption: Returning visitors can send application data in the very first packet.
Google's data shows QUIC reduced YouTube buffering by 18% and decreased search page load time by 8%. Behind these numbers lies a tectonic shift at the transport layer.
The "Disappearance" and Rebirth of SSL/TLS
In the traditional stack, TLS sits as a distinct security layer atop TCP. QUIC’s revolution is weaving security directly into the transport fabric. TLS 1.3 isn't a layer on top of QUIC; it's an integrated component.
This integration creates a counterintuitive reality: SSL/TLS is becoming less visible as a standalone product but more critically important than ever. Encryption and transport are now inseparable from the initial design.
This brings us to the security cost of 0-RTT. To enable zero-round-trip resumption, QUIC allows clients to send application data in the very first packet, using keys from a previous session. This introduces replay attack risks: an attacker could intercept and resend that initial request packet. Consequently, QUIC mandates that 0-RTT data must be idempotent—replaying it must cause no side effects. This imposes new requirements on API design: a GET request is fine for 0-RTT; a POST payment request must use a secure 1-RTT connection.
The implication is profound: developers and architects must now ask, "Which of my APIs are idempotent?" Security considerations are shifting left, from ops configuration to protocol and API design.
Server Kernels & The Great "De-Optimization"
For two decades, a core tenet of server optimization has been: push network processing into the kernel. From TCP Offload Engine (TOE) NICs to kernel-bypass techniques, the goal was to minimize user-kernel context switches. QUIC, running entirely in user-space, turns this on its head.
This grants unprecedented flexibility. Engineers at Cloudflare can iterate on their QUIC implementation, patch vulnerabilities, and add features—all without touching the OS kernel. However, all encryption, congestion control, and packet reassembly now occur on user-space CPUs, increasing computational load.
Early benchmarks indicate QUIC can consume 2-3x more CPU than TCP+TLS 1.3 for equivalent traffic. This isn't just about needing more servers; it's a fundamental shift in computational budgeting. Future servers may require:
Greater single-core performance over more cores (QUIC connection state is complex).
Dedicated optimizations for user-space networking stacks (e.g., DPDK support).
A redesign of hardware acceleration—from TCP offload to QUIC crypto offload.
CDN's Identity Crisis: Redefining the Intelligent Edge
A core value proposition of traditional CDNs has been TCP-based intelligent routing: measuring connection time, latency, and packet loss to dynamically select the best path. QUIC changes the game.
First, QUIC's connection migration complicates the logic of "binding" a user to an edge node via IP. The user's IP may change, but the QUIC Connection ID persists. How does the CDN track and maintain session state? New state-management mechanisms are needed.
Second, many classic TCP optimizations are becoming irrelevant. The proprietary congestion control algorithms, buffer tuning, and loss recovery mechanisms that CDNs invested in heavily offer diminishing returns against UDP-based QUIC. New competitive battlegrounds are emerging:
The efficiency and quality of QUIC implementation (which varies greatly between providers).
The ability to process 0-RTT requests at the edge.
Session persistence during network handovers.
The ultimate shift may be the accelerated evolution of CDNs from "smart pipes" to "distributed compute platforms." If most transport complexity is encapsulated end-to-end in QUIC, edge nodes can focus more on computation—running business logic closer to users, not just optimizing transport.
The Hybrid-Protocol Hell: A Debugging Nightmare
The real world won't flip a switch to HTTP/3. We face years of hybrid-protocol coexistence. Browsers will dynamically shift between HTTP/1.1, HTTP/2, and HTTP/3 based on network conditions and server support. This means:
Your monitoring must comprehend three distinct protocol stacks. A user on Chrome may succeed via HTTP/3, while another behind a corporate firewall on the same network fails back to HTTP/2 or even HTTP/1.1—because the firewall might block UDP port 443.
More subtle is the performance attribution problem. When a user reports "the site is slow," you must diagnose: Is it a bug in the QUIC implementation? Misconfigured TCP tuning? Or a middlebox interfering with UDP? Most existing APM tools are built around TCP, with immature observability for QUIC.
Operations teams face a dual burden: maintaining expertise in a slowly obsolescing skill (TCP tuning) while mastering an emerging, not-yet-mature one (QUIC debugging). This transitional period may last 3-5 years, accruing significant technical and cognitive debt.
The Architectural Mindset Shift: From Layered to Vertical
Traditional network thinking is layered and modular: physical, IP, TCP, TLS, HTTP… each layer is independent and optimizable. QUIC shatters this clean separation.
The future infrastructure architect needs a new mental model:
The Inseparability of Transport and Security: You can no longer optimize "networking" and "security" in isolation; they are two sides of the same coin.
Dynamic Protocol Version Compatibility: Systems must gracefully handle the entire spectrum from HTTP/1.1 to HTTP/3, not optimize for one.
The Primacy of User-Space Performance: Server selection and configuration must be re-evaluated for single-core performance and user-space processing efficiency.
Protocol-Aware Observability: Monitoring tools must understand QUIC semantics to trace performance issues across protocol versions.
Your Roadmap: Preparing for the HTTP/3 Era
If you don't want to be left behind, here is a practical, phased approach:
Phase 1: Assess & Experiment (Months 1-3)
Use Cloudflare's HTTP/3 Test Tool to check your site's support status.
Enable HTTP/3 in a staging environment and gather performance baselines.
Engage your CDN provider on their QUIC implementation roadmap and performance metrics.
Phase 2: Harden Protocol Compatibility (Months 3-6)
Audit your API design. Clearly distinguish idempotent operations (safe for 0-RTT) from non-idempotent ones (require 1-RTT).
Upgrade monitoring to distinguish and track traffic for HTTP/1.1, HTTP/2, and HTTP/3.
Work with security teams to assess 0-RTT replay risks and develop mitigation policies.
Phase 3: Architect for Gradual Migration (Months 6-18)
Prioritize HTTP/3 for mobile apps and APIs, where the benefits are most pronounced.
Evaluate modern load balancers that support dual-stack (TCP + QUIC) operation.
Start building team competency in QUIC protocol principles and debugging methodologies.
The migration from TCP to QUIC is more than a technical protocol swap; it's a fundamental re-architecting of the internet's communication model. It transforms three decades of network optimization wisdom from "valuable asset" into "technical debt."
The true insight is this: every revolution at the protocol layer redistributes value within the computing ecosystem. When transport becomes intelligent and reliable by default, the center of gravity for computation migrates to the edge. When security is a protocol's native property, the security expert's role evolves from "gatekeeper" to "architect."
Your server strategy, your SSL posture, your CDN logic—the seemingly solid technical decisions of today are being quietly redefined by a revolution that began on UDP port 443. This isn't speculation; it's the unfolding present.
The wisest stance isn't resistance but comprehension. Understand that this protocol shift isn't merely optimizing a network; it's redefining the very meaning of a "connection." When connections become seamlessly mobile, instantly resumable, and inherently secure, we gain unprecedented freedom to reimagine how applications and services are built.
The teams that first understand and adapt to this new paradigm won't just gain a performance edge. They will acquire the architectural capital to reimagine digital services. And that—the catalytic potential for innovation at the application layer—is the most profound gift of the QUIC revolution.

