Why HTTPS is Mandatory: Understanding the Foundational Security Role of SSL Certificates
Let's be brutally honest for a moment. That little padlock in your browser's address bar? Most of us click past it without a second thought. We've been trained to look for it, but few of us truly understand the monumental, invisible war it represents—a war fought not with weapons, but with mathematics, global trust systems, and an intricate dance of protocols that quietly protects every login, every purchase, and every private message you send online.
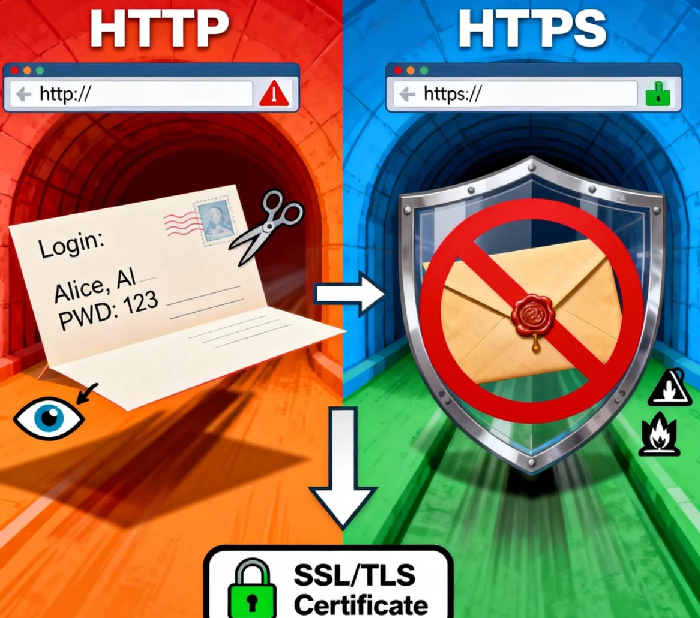
HTTPS is not a "nice-to-have" feature anymore; it's the absolute, non-negotiable bedrock of the modern web. The shift from HTTP to HTTPS marks the evolution of the internet from a naive, open postcard system to a sealed, verified, and armored courier service. At the heart of this transformation is the humble yet mighty SSL/TLS certificate—a technology that does far more than just "encrypt."
The Illusion of a Simple Lock: A Triad of Protections
We often simplify HTTPS to "the secure version of HTTP." While true, this misses the profound, three-fold crisis it solves. Imagine sending a confidential letter via standard mail (HTTP). Anyone handling it can read it (eavesdropping), alter its contents (tampering), or even send a forged reply pretending to be your intended recipient (impersonation).
This was the chaotic reality of the early web. HTTPS, enforced by an SSL certificate, solves all three in one elegant swoop:
Encryption (Privacy): It scrambles the data between you and the website into gibberish for anyone intercepting it.
Authentication (Identity): It provides a digital ID card, proving you're connected to "example.com" and not a clever fake.
Integrity (Trust): It ensures that the scrambled data isn't altered in transit without breaking the connection.
The stakes are no longer theoretical. Studies show that over 75% of users will immediately abandon a site if their browser shows a "Not Secure" warning. HTTPS has become the basic price of admission for user trust.
The Hidden Hierarchy: Not All Padlocks Are Created Equal
Here's where it gets interesting. That padlock can represent three very different levels of verification, a hierarchy most businesses misunderstand at their peril.
Domain Validation (DV): The basic model. The Certificate Authority (CA) only checks if you control the domain. It's like getting a PO box—it proves you have access to a location, but not who you are. Perfect for a personal blog.
Organization Validation (OV): A significant step up. The CA verifies the actual legal identity behind the organization requesting the certificate. This information is embedded within the certificate itself. It's a verified business license for your website.
Extended Validation (EV): The gold standard. The CA conducts a rigorous, standardized vetting process of the entity's legal, physical, and operational existence. For years, this triggered the prominent green address bar with the company name.
The Counter-Intuitive Twist: While browsers have recently de-emphasized the visual green bar for EV, its value hasn't diminished; it has simply shifted. The rigorous audit trail and legal identity assurance make EV certificates critical for high-value sectors like finance, e-commerce, and legal services. They are less about showing off trust to users and more about legally upholding trust and meeting compliance requirements. The data is clear: sites dealing with sensitive data that upgrade to OV or EV certificates see measurable reductions in cart abandonment and increases in conversion, as they subtly weed out sophisticated phishing attempts.
The Invisible Engine: Six Technologies in a Delicate Dance
The magic of an SSL certificate isn't a single trick. It's a precise choreography of six cryptographic technologies working in concert. Understanding this demystifies the "how."
Asymmetric Encryption (The Handshake): Uses a public/private key pair. The server's public key (in the certificate) encrypts data that only its private key can decrypt. This sets up the initial secure channel.
Symmetric Encryption (The Workhorse): Once the secure channel is established, a faster, single "session key" is generated to encrypt the bulk of the data.
Digital Signatures (The Tamper Seal): Proves a message (or certificate) came from the holder of the private key and wasn't altered. This is the core of authentication.
Certificate Authority (The Trust Anchor): The trusted entity that issues and digitally signs the certificate, vouching for the binding between a public key and the server's identity.
Certificate Revocation (The Emergency Brake): Mechanisms like CRL and OCSP that allow a compromised certificate to be invalidated before its expiry date.
The Handshake Protocol (The Conductor): The step-by-step process that orchestrates all the above to establish a secure TLS connection.
This complex dance happens in milliseconds during the "TLS Handshake." When one element is weak—like a compromised CA or a flawed encryption algorithm—the entire system is at risk.
Beyond the Browser: The Ripple Effects You Never See
The impact of SSL extends far beyond the padlock. It silently shapes the digital ecosystem in powerful ways.
1. The SEO Imperative: In 2014, Google confirmed HTTPS as a ranking signal. But the real impact is more nuanced. A secure site enjoys lower bounce rates and longer dwell times—positive user engagement signals that Google's algorithms heavily favor. Furthermore, many cutting-edge web platform features (like geo-location, progressive web app functionalities, and even some JavaScript APIs) require a secure context. By not using HTTPS, you're not just risking a minor ranking dip; you're locking your site out of the future of web capabilities.
2. The Performance Myth, Busted: A persistent misconception is that HTTPS slows down your site. The overhead of the initial handshake is minimal, especially with modern TLS 1.3, which is faster than its predecessors. The encryption itself is handled by efficient hardware. In reality, the performance benefits of HTTP/2 and HTTP/3—protocols that significantly speed up page loading—are almost exclusively supported over HTTPS. Going secure often makes your site faster.
3. The Trust Chain and the Fragile Web of PKI: Our collective trust in HTTPS rests on the Public Key Infrastructure (PKI). This is a global hierarchy where a handful of "Root CAs" are implicitly trusted by your browser or operating system. Every website certificate ultimately chains back to one of these roots. This system, while robust, creates central points of failure. A breach at a major Root CA could theoretically undermine trust for millions of sites—a stark reminder that online security is a shared responsibility held together by protocol, constant auditing, and vigilance.
The Free vs. Paid Fallacy: A Strategic Choice, Not Just a Financial One
The rise of non-profits like Let's Encrypt, which provide free DV certificates, has been a revolution for web security. It has made basic encryption ubiquitous. However, this has bred a dangerous new myth: "All certificates are the same."
This is a critical strategic error for any business. The choice between a free DV certificate and a paid OV/EV certificate is not about the strength of the encryption (256-bit encryption is standard). It's about the strength of the identity verification.
For a business, an OV or EV certificate is a liability shield and a trust signal. In the event of a sophisticated phishing attack that spoofs your domain, a validated certificate makes it harder for the fake site to appear legitimate to more discerning users and security software. It's an investment not in technology, but in your brand's digital reputation. In a world where 43% of cyber attacks target small businesses, this layer of verified identity is not an IT expense; it's a business continuity investment.
So, the next time you see that padlock, see it for what it truly is. It is not merely a icon. It is the silent, functional output of a vast, interconnected system—a system where advanced mathematics provides the raw material, meticulous global standards provide the blueprint, and continuous human auditing provides the guardrails.
HTTPS is mandatory because the internet we rely on for our social connections, our commerce, and our information cannot function without foundational trust. The SSL certificate is the engineer of that trust. It is the reason you can confidently type your password, enter your credit card details, or share private thoughts online. In the digital age, it is more than a protocol; it is the very oxygen of trust—invisible, vital, and, once you understand its role, utterly indispensable.
Now, ask yourself: does your online presence breathe this essential trust, or is it holding its breath in an insecure past?

