Beyond Security Config: Auditing Your Defenses with an Attacker's Mindset
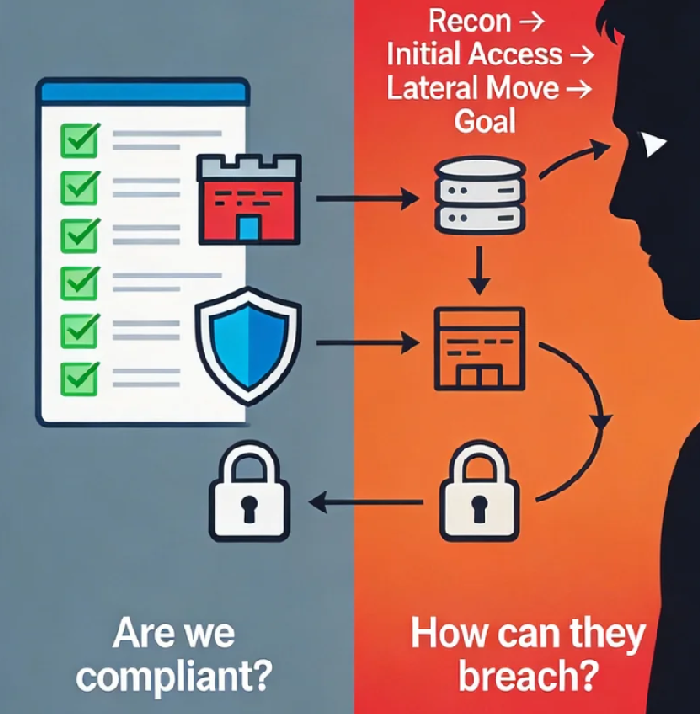
Let's be honest. You've probably spent countless hours configuring firewalls, patching vulnerabilities, and enforcing complex password policies. Your security dashboard is a sea of green checkmarks, and your compliance reports are impeccable. Then, one Tuesday morning, you get the call: there's been a breach. The investigation reveals the attacker didn't brute-force your firewall or crack your 16-character password. They slipped through a gap you never thought to look at—a forgotten API endpoint, a misconfigured cloud storage bucket, or an overly trusted service account.
This scenario isn't failure; it's a fundamental mismatch in perspective. You've been building and auditing your defenses with a Defender's Checklist, a static, inside-out view focused on "Are our settings correct?" Meanwhile, the adversary operates with an Attacker's Mindset, a dynamic, outside-in pursuit of a single question: "What's the path of least resistance?"
Industry data paints a stark picture. A 2023 study by IBM found that over 80% of successful breaches exploited vulnerabilities for which a patch was available but not applied. More tellingly, in nearly 70% of cases, the initial entry point was not a sophisticated zero-day but a misconfiguration or credential theft. Our defenses are failing not because we lack tools, but because we lack the right lens to see their weaknesses. It's time to put down the checklist and learn to think like the adversary. This isn't about becoming a hacker; it's about becoming a smarter defender.
The Cognitive Shift: From "Secure Configuration" to "Exploitable Pathway"
The defender's world is built on policies and compliance. We ask: "Is the password policy enabled? Are ports 22 and 3389 filtered? Are we on the latest patch tier?" This creates a fortress with thick walls but perhaps an unlocked side door.
The attacker's world is built on psychology and physics. They ask:
"What do they have that I want?" (Asset/Data)
"What can I see from the outside?" (Reconnaissance)
"What's one thing that's out of place or weakly held?" (Initial Foothold)
"If I'm here, where can I go next?" (Lateral Movement/Persistence)
The core insight is this: Security is not a state achieved by configuration; it's a property emerging from the absence of exploitable pathways. Your firewall rule is only as strong as the weakest trust relationship behind it.
Core Principle #1: Assume Breach — The Liberating Perspective
The most powerful—and unnerving—principle of the attacker mindset is Assume Breach. Stop asking, "How do we keep them out?" Start asking, "What if they're already in?"
This is not defeatism; it's strategic realism. It shifts your entire security posture from purely preventative to deeply detective and responsive. When you operate under Assume Breach:
Your log collection is no longer a compliance task but a forensic lifeline.
Internal network segmentation isn't just nice-to-have; it's critical to containing an intruder's "blast radius."
You stop focusing solely on the perimeter and start hunting for anomalous internal activity—a server talking to a rare external IP, a user account logging in at 3 AM from a new country.
This principle shatters the checklist mentality. A checklist might verify that anti-virus is installed. Assume Breach asks, "If malware is running, how would we know, and how would we stop it from calling home?"
Core Principle #2: Follow the Attack Chain, Not the Vulnerability List
Defenders think in lists of CVEs (Common Vulnerabilities and Exposures). Attackers think in TTPs (Tactics, Techniques, and Procedures) strung together into a Kill Chain.
Frameworks like MITRE ATT&CK codify this attacker logic. It's not about one vulnerability; it's about the story: Initial Access → Execution → Persistence → Privilege Escalation → Defense Evasion → Discovery → Lateral Movement → Exfiltration.
Your audit must mirror this. Don't just ask, "Is SQL injection blocked at the WAF?" (a single technique). Ask:
"If an attacker phished a marketing employee (Initial Access), could they run a script (Execution)?"
"Could they then steal the developer's SSH keys from the memory (Credential Access) and move to the staging server (Lateral Movement)?"
"Would our logs correlate these disparate events across different systems?"
This reveals that a medium-severity vulnerability in the marketing CMS, combined with weak file permissions on a shared drive, can be a more critical risk than a high-severity bug in an internally isolated backup server. You're now auditing for narrative risk, not just individual flaws.
Core Principle #3: Understand the Adversary's "Business Model"
Not all attackers are the same. Their goals and constraints define their methods. Your defense audit must account for this.
The Script Kiddie & Commodity Ransomware Gang: They are automated, noisy, and opportunistic. They spray-and-pray, looking for known, unpatched vulnerabilities (like ProxyShell or Log4j). Your primary audit question here is: "Are we as hardened as the average target?" Patching speed and baseline hygiene (closed RDP, strong passwords) are your best defense.
The Targeted Adversary (APT or Competitor): They are patient, stealthy, and resourceful. They will study you, craft spear-phishing emails, and invest in custom malware. Your audit question shifts to: "What is our crown jewel data, and what unique, trusted paths lead to it?" This demands auditing for over-privileged service accounts, excessive internal trust, and monitoring for low-and-slow data exfiltration.
By profiling your likely adversaries, you prioritize your audit findings. You might accept the risk of a bug in an internal tool (low value to a ransomware gang) but go to extreme lengths to isolate and monitor your financial database cluster.
Practical Audit: Applying the Mindset to Your Defenses
Now, let's put on the hat. Let's audit a classic, checklist-secured environment with our new mindset.
1. The "Hardened" Web Server:
Checklist View: Apache is on the latest version. ModSecurity WAF rules are active. Root login is disabled. All green.
Attacker Mindset Audit: You find the
/server-statuspage is enabled (a common default for performance monitoring). It's not a "vulnerability," but it leaks internal IPs, worker threads, and request patterns—gold for reconnaissance. You also find the backup script in/opt/runs as root and includes a database password in plain text. Attack Path Identified: Recon via/server-status→ Identify app structure → Find backup script → Steal DB credentials → Move laterally to database.
2. The "Compliant" Cloud Environment:
Checklist View: Security groups block unnecessary ports. S3 buckets have encryption enabled. IAM roles are used.
Attacker Mindset Audit: You use a tool like
pacuvmto list all resources. You find an S3 bucket namedcompanyname-backupswith "List" permissions open to the world (s3:ListBucket). It doesn't allow file download, but an attacker can now see all backup filenames, which might reveal structure likeprod-db-2024-05-15.sql.gz. This is intelligence for a targeted attack. Attack Path Identified: Discover open bucket → Map backup naming scheme → Plan attack to compromise system that generates these backups.
From Audit to Culture: Building a "Purple Team" Reality
This mindset cannot live with one person. It must become an organizational muscle through Purple Teaming.
Blue Team: The traditional defenders (SOC, incident response).
Red Team: The ethical attackers who simulate breaches.
Purple Team: The collaborative fusion of both. The Red Team shares their TTPs and attack narratives in real-time; the Blue Team tests their detection and response against them. It's a continuous feedback loop, turning every simulated attack into a direct lesson for the defenders.
Implementing this means shifting from annual penetration tests (a point-in-time snapshot) to ongoing exercises where the goal isn't to "pass or fail," but to learn and adapt. It turns security from a cost center into a dynamic, adaptive capability.
So, the next time you review your security posture, silence the checklist in your mind for a moment. Step outside your digital walls. Look at your own infrastructure not as its architect, but as a hunter.
Ask the simple, profound questions: "If I wanted to steal X, where would I start? What looks out of place? What trusts what too much?" This shift—from configuring to interrogating, from assuming safety to assuming compromise—is what separates a maintained system from a resilient one.
The goal is no longer an unbreachable fortress (a fantasy). The goal is an environment where intrusions are expected, quickly discovered, effectively contained, and turned into lessons that make you stronger. In the endless chess game of cybersecurity, thinking only as the defender guarantees a loss. Start thinking like an attacker, and you finally begin to play both sides of the board.

