The Hacker's "To-Do List": Reverse-Engineering Your Proactive Defense Playbook
It’s 2:17 AM. Your phone buzzes, not with a mundane notification, but with a critical alert from your SIEM. A server in your production cluster is making DNS queries to a domain that looks like random garbage. Your heart sinks. You log in, adrenaline pumping. The firewall logs show nothing blocked. The IDS is quiet. The latest vulnerability scan from last week was clean. Yet, there it is—a slow, steady trickle of encoded data leaving your network, has been for days. The attacker didn’t smash through your front door; they found a forgotten window you didn’t even know was unlocked.
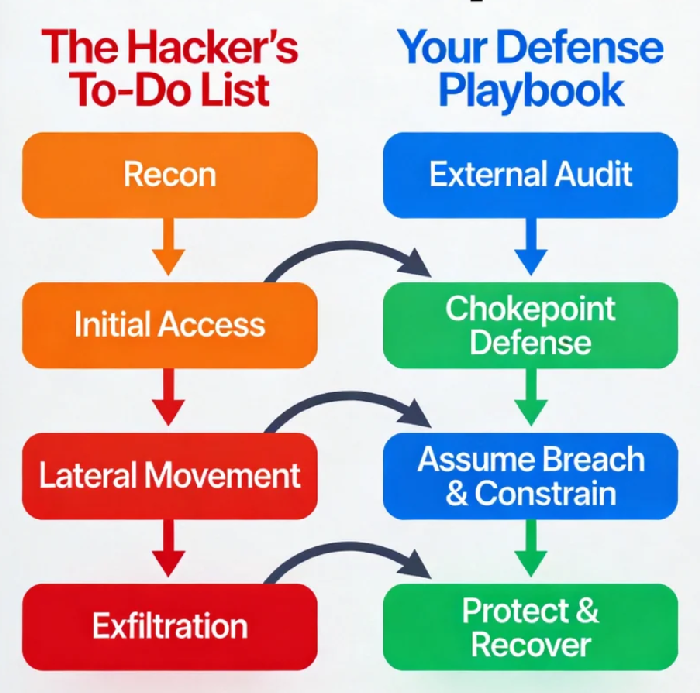
This scenario isn’t a failure of your tools, but a failure of perspective. You’ve been defending a blueprint of your own network, following a checklist of best practices. The attacker, however, wasn’t following your checklist. They were executing theirs—a pragmatic, goal-oriented "To-Do List" focused solely on the path of least resistance from the internet to your crown jewels.
The uncomfortable truth, backed by studies from firms like Mandiant, is that the median "dwell time"—the period an attacker goes undetected inside a network—still spans weeks. This isn’t because defenses are weak in a conventional sense, but because we defend places, while attackers exploit paths. To shift from being a victim of their list to the author of their failure, you must learn to read it backward. This is the essence of building a proactive defense: not by guessing what they might do, but by understanding what they must do, and being there to meet them.
The Mindset Shift: From Defender's Checklist to Attacker's Workflow
The defender’s world is built on compliance and configuration. Our internal monologue asks: Are the ports closed? Is the AV updated? Are the passwords complex? This creates a static fortress, a snapshot of "secure" at a point in time.
The attacker’s world is governed by tactics, techniques, and procedures (TTPs). Their internal monologue is a series of operational questions: What’s the target? What can I see? What’s the easiest way in? If I’m here, where can I go next? Their "To-Do List" is a dynamic, iterative workflow, formalized in frameworks like the MITRE ATT&CK® matrix, which catalogs the real-world behaviors of adversaries.
Your mission, should you choose to accept it, is to reverse-engineer this list. Don’t just build a wall; study the climbing techniques of every thief who wants to get over it, and coat the top in oil, string tripwires at the footholds, and put motion sensors on the other side.
Stage 1: Reconnaissance & Weaponization — The "Shopping List"
Their Goal: Answer "What's there to hit?" and "What's my best tool for the job?"
This isn’t just scanning; it’s profiling. Attackers scour LinkedIn for tech stack hints, GitHub for leaked API keys or hard-coded passwords, and use tools like Shodan to find every internet-facing asset you own—including that legacy FTP server from 2015 the infra team forgot about. They’re building a map of your digital attack surface, and they’re alarmingly good at it. A 2023 report found that over 70% of organizations have at least one unknown, exposed asset that could serve as an entry point.
Your Reverse-Engineered Defense: The External Audit Play
Action: Become your own adversary. Regularly commission or conduct external penetration tests and "bug bounty" style assessments. But go deeper: run continuous attack surface management (ASM) scans. You need to see what they see.
Key Move: Implement robust threat intelligence feeds. Don’t just look for generic malware signatures; look for indicators that someone is scouting you—repeated scans from the same IP range, DNS reconnaissance against your domain names.
Philosophy: Security begins long before the first exploit attempt. Minimizing your public footprint and poisoning their reconnaissance data are first-order wins.
Stage 2: Initial Access & Execution — The "Lockpick & Entry"
Their Goal: Get a persistent foothold inside the environment.
This is where the "how" meets the "what." They’ll use the vulnerability on your unpatched internet-facing web server (your IT team deferred the patch due to "application stability concerns"). Or, they’ll send a frighteningly convincing phishing email to an accountant, crafted using details gleaned from Stage 1, to deliver a malicious document. Verizon’s DBIR consistently highlights that over 80% of breaches involve the use of stolen credentials or phishing.
Your Reverse-Engineered Defense: The Chokepoint Play
Action: Harden the inevitable entry points. Assume some phishing will succeed and some vulnerabilities will be missed.
Key Move:
Relentless Patching: Prioritize patches for internet-facing systems with a ruthless, metrics-driven SLA.
Application Allowlisting: Don’t just try to block bad software; define and permit only known-good software to run on critical systems.
Multi-Factor Authentication (MFA) Everywhere: Especially for email, VPN, and cloud consoles. This single control can invalidate vast numbers of stolen credentials.
Philosophy: Make initial access costly, noisy, and unlikely to grant immediate value. An attacker stuck at this stage is a frustrated attacker.
Stage 3: Persistence, Privilege Escalation & Lateral Movement — The "Infiltration & Expansion"
Their Goal: Become "native," move toward the target, and ensure they can stay.
The first compromised machine is often just a beachhead. Now, they'll dump password hashes from memory, exploit misconfigurations in internal file shares (Everyone: Full Control is a classic), or abuse legitimate admin tools like PowerShell or PsExec to move silently. They seek domain admin rights—the keys to the kingdom. This stage is where traditional, perimeter-focused security truly blindsides you; it all looks like "internal traffic."
Your Reverse-Engineered Defense: The Assume Breach & Constrain Play
Action: Architect your network to limit the "blast radius" of any single compromise.
Key Move:
Zero Trust Segmentation: Move beyond simple VLANs. Micro-segment your network so that a compromised web server cannot directly talk to your domain controller or financial database. Every connection request is verified.
Privileged Access Management (PAM): Tightly control and monitor the use of admin accounts. No more shared passwords; use just-in-time, audited elevation.
Endpoint Detection & Response (EDR): This is non-negotiable. You need tools that can spot the behavior of lateral movement—unusual SMB connections, scheduled tasks being created remotely, hash-dumping activity—not just known malware files.
Philosophy: The network inside your firewall should not be a trusted free-for-all. Constrain, monitor, and verify all internal movement.
Stage 4: Exfiltration & Impact — The "Heist & Cover-Up"
Their Goal: Achieve the mission (steal data, deploy ransomware) and erase their tracks.
Data is siphoned out slowly, disguised as normal HTTPS traffic. Ransomware is deployed, encrypting files. Then, they use built-in system tools to clear event logs. They’re counting on your lack of centralized logging and your backup system being online and accessible (and thus also encrypted).
Your Reverse-Engineered Defense: The Protect the Crown Jewels & Prepare Play
Action: Focus on what matters most and ensure resilience.
Key Move:
Data-Centric Security: Identify your true "crown jewels." Encrypt this data at rest and rigorously control access with more stringent policies.
Aggressive Egress Filtering: Monitor outbound traffic for large, unusual transfers to unfamiliar external IPs or cloud storage domains.
Immutable, Offline Backups: Your backup strategy must follow the 3-2-1 rule (3 copies, 2 media types, 1 offsite), with at least one copy being immutable (cannot be altered or deleted) and physically disconnected from the network. Test restoration quarterly.
Philosophy: Assume they will reach some data. Your final line of defense is making that data useless to them (encryption) and ensuring their ultimate weapon (ransomware) is rendered moot by reliable recovery.
Assembling Your Proactive Playbook: The Continuous Cycle
This reverse-engineering isn’t a one-time project. It’s an operational discipline—a playbook that lives and breathes.
Map & Adopt: Align your defenses explicitly to the MITRE ATT&CK framework. For each technique in the matrix relevant to your tech stack, ask: "How do we prevent this? How would we detect it if prevention fails? How would we respond?"
Embrace Purple Teaming: Move beyond annual penetration tests. Run continuous purple team exercises where your red (attack) team simulates specific TTPs and your blue (defense) team practices detection and response in real-time. The goal is learning, not a pass/fail grade.
Measure What Matters: Ditch vanity metrics like "number of blocked IPs." Start measuring critical security controls: "Mean Time to Detect (MTTD)" and "Mean Time to Respond (MTTR)." Your goal is to shrink these numbers relentlessly by refining the playbook born from the hacker's list.
So, tonight, when you review your security dashboard, don't just look for red flags. Look for the absence of the right green ones—the indicators that your reverse-engineered defenses are actively hunting. Don't ask, "Are we compliant?" Ask, "If a skilled attacker added us to their to-do list today, which item would be easiest for them to check off?"
Then, go make that item impossibly hard. The goal is not an impenetrable fortress—a fantasy in a connected world. The goal is to make the cost and risk of attacking you so high, and the likelihood of their success so low, that you get moved from the "Target" column to the "Too Hard" pile. That is the ultimate victory, and it starts by thinking not as a defender, but as a student of the attack.

