Beyond Defense: Transforming Security into a Core Business Competency
Let's start with a question that might make you uncomfortable: When was the last time your security team was invited to a product strategy meeting, not as a gatekeeper to say "no," but as a strategic partner to help figure out "how"?
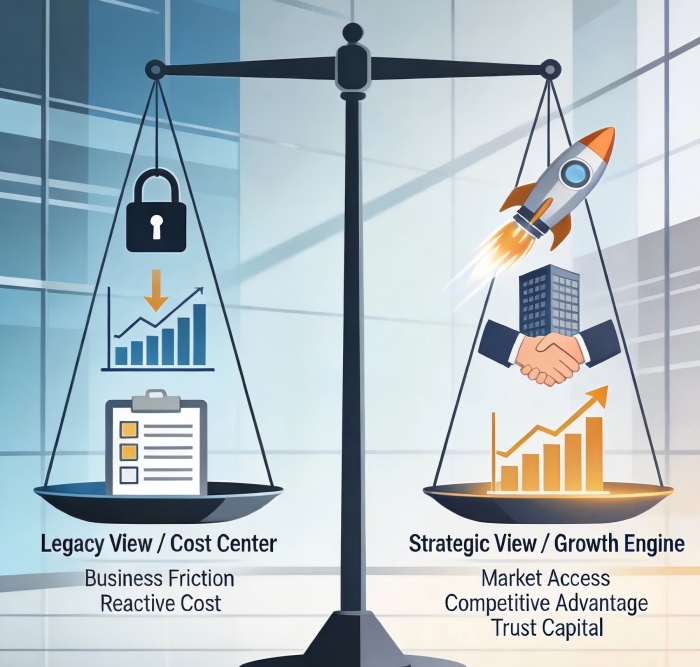
If the answer is "never" or "rarely," you're experiencing the central paradox of modern cybersecurity. We've invested millions in firewalls, trained our teams on the latest threats, and built complex compliance frameworks, yet security remains locked in the organizational basement—a cost center, a necessary evil, a department whose primary success metric is the absence of disaster. We measure what we prevent, not what we enable.
This mindset is not just outdated; it's a strategic liability. In the digital-first economy, security is no longer just about protection—it's about acceleration. The most forward-thinking companies aren't just using security to defend their business; they're wielding it to define their business. They've realized that in a world where data is the new oil and trust the ultimate currency, robust, transparent security isn't an expense on the balance sheet; it's the engine on the competitive balance sheet.
Consider this: A 2023 survey by a leading consultancy found that 74% of enterprise buyers now list "security posture" as a top-three criterion when selecting a SaaS vendor, often ahead of price. Another study revealed that companies that proactively communicate their security investments and certifications experience up to a 15% premium in customer trust and retention. The message is clear. The market is no longer just buying your product; it's buying your promise of integrity. Security has moved from the server room to the boardroom, and finally, to the marketplace.
The Great Reframe: From "Business Enabler" to "Business Creator"
The first step in this transformation is a linguistic and conceptual shift. We must retire the well-meaning but insufficient term "business enabler." An enabler is passive—it allows something else to happen. A true competency is active; it makes things happen.
Think of it through a classic business lens: Finance isn't just an "enabler" because it pays the bills; it's a core competency that manages capital for strategic growth. Marketing isn't just an "enabler" of sales; it creates market demand and defines brand value. Security must ascend to the same tier. It's not merely about enabling digital operations to proceed without incident; it's about actively creating Market Access, Innovation Velocity, and Trust Capital.
Dimension 1: Security as the Key to Market Access (The New Digital Passport)
Global regulation—GDPR, CCPA, sector-specific rules in finance and healthcare—has erected a series of digital border controls. Compliance is no longer a checkbox for legal; it's a non-negotiable passport for entering lucrative markets.
Progressive organizations don't just scrape by with minimum viable compliance. They use security maturity as a competitive wedge. They pursue certifications (SOC 2 Type II, ISO 27001) not as trophies, but as sales collateral. Their security team works hand-in-hand with the sales engineering unit, crafting sections of the RFP response that don't just answer security questions but tell a story of unparalleled diligence. In this model, the CISO's budget is partially funded by the revenue from deals where their team's work was the decisive factor. Security transitions from a cost center to a profit-center contributor.
Dimension 2: Security as an Innovation Accelerator (Shifting Left, Moving Faster)
The old model of "throw it over the wall to security at the end" is a recipe for delays, frustration, and technical debt. The "Shift Left" movement is often misunderstood as just pushing testing earlier. Its true power is cultural integration.
When security architects are embedded in product design sprints, they don't just say "that's insecure." They ask, "What are you trying to achieve, and how can we build that securely from the ground up?" This eliminates the 100x cost multiplier of fixing bugs in production. More importantly, it fosters the development of "Secure by Design" as an R&D principle. The result isn't a slower development cycle; it's a more predictable and efficient one. Security becomes the guardrails on the highway, not the stop sign at the end of the road, allowing the business to innovate at full speed with confidence.
Dimension 3: Security as Resilience & Trust Capital (The Ultimate Brand Insurance)
A breach's direct costs—fines, remediation—are just the tip of the iceberg. The real damage is to customer trust and brand equity, which can take years to rebuild. Thus, cybersecurity resilience is a direct contributor to brand valuation.
Companies that operationalize this view treat their security program as a form of corporate reputation insurance. They don't hide their security posture; they selectively and intelligently communicate it. They understand that in an era of constant threats, demonstrating operational resilience and transparent response plans is a powerful market differentiator. For their customers, partners, and investors, this cultivated trust becomes a tangible asset—a moat that competitors cannot easily cross.
Measuring the Immovable Object: Quantifying Security's Business Value
To cement this new status, security must speak the language of business: metrics that matter in the C-suite. This means moving beyond "number of blocked attacks" and "patch compliance rate."
We need a dashboard that speaks to Business Value:
Revenue Enablement: Value of contracts won where security certification was a mandatory or deciding factor.
Time-to-Market Acceleration: Reduction in development cycle time attributed to integrated DevSecOps practices and eliminated security rework.
Risk Quantification: Modeled financial impact of incidents avoided (beyond just technical detections), expressed in potential saved fines, lost revenue, and brand repair costs.
Customer Trust Metrics: Correlation between security transparency (e.g., published audit reports) and customer retention rates or willingness-to-pay premiums.
When a security leader can walk into a CFO's office and say, "Our program directly contributed to $5M in new enterprise deals last quarter and reduced projected product launch delays by 30%," the conversation fundamentally changes.
The Four-Stage Evolution: A Practical Roadmap
Transforming security doesn't happen overnight. It's a deliberate evolution through distinct stages of maturity.
Stage 1: Align (From Cost to Enabler)
Focus: Link security objectives to one clear business goal (e.g., "support the launch in the EU market").
Action: Security engages with product and legal teams before the final design to ensure GDPR compliance is baked in, not bolted on.
Success Signal: The business unit views security as a helpful guide, not a police officer.
Stage 2: Integrate (From Enabler to Differentiator)
Focus: Make security a visible component of the product and customer experience.
Action: Develop unique security features (e.g., customer-controlled encryption keys) for the sales pitch. Publish a clear, plain-language trust center.
Success Signal: Marketing starts citing security capabilities in campaigns. Sales proactively brings security experts to customer meetings.
Stage 3: Lead (From Differentiator to Core Competency)
Focus: Security drives new business initiatives.
Action: The security team architects a new "Security Posture Management" service sold to existing clients. The CISO has a regular slot at Board meetings to discuss strategic risk and opportunity.
Success Signal: Security is a budget line item in new business proposals. The company is cited by analysts for security innovation.
Stage 4: Scale (From Competency to Ecosystem Advantage)
Focus: Export security excellence to build a more robust and loyal ecosystem.
Action: Provide security frameworks and tools to key suppliers, raising the collective resilience of the supply chain. Lobby for industry standards based on internal best practices.
Success Signal: The company's security model attracts top talent and strategic partners, creating a sustainable competitive advantage.
The journey to transforming security is, at its heart, a journey of re-perception. It’s about seeing the firewall not just as a barrier against threats, but as the foundation of a trust platform. It’s about recognizing that the security team’s deepest expertise isn't in configuring rules, but in understanding systemic risk and resilience—a skill that is invaluable for navigating any modern business landscape.
The question for leaders is no longer, "Can we afford to invest in security?" The imperative question has become, "Can we afford not to leverage security as a primary driver of our growth, trust, and innovation?" In the race to win the future, the organizations that will pull ahead are those that realize their cybersecurity team doesn't just carry a shield. They hold a compass, a blueprint, and ultimately, the keys to the kingdom.

