Your Security Debt Balance: A Practical Framework for Assessment and Remediation
Let's be honest for a second. You know that nagging feeling in the back of your mind? The one that whispers about the unpatched legacy server in the corner, the shared admin password on a Post-it note (digitally or otherwise), or the overly permissive cloud storage bucket you created for a "quick test" six months ago? That feeling isn't just anxiety; it's your subconscious tallying up your Security Debt.
Forget for a moment the external hackers with their fancy zero-days. The most likely threat to your organization is already inside the walls, not as a malicious actor, but as a silent, accumulating liability. Security Debt is the sum of all the postponed security tasks, accepted risks, temporary configurations, and outdated systems that you know you should fix but never quite get to. It’s the technical debt of the security world, but with a crucial difference: where technical debt charges interest in developer hours and system fragility, security debt accrues "risk interest," payable in the currency of breaches, data loss, and reputational ruin.
The data is sobering. Studies, such as those cited in Verizon's annual reports, consistently show that over 60% of successful breaches exploit vulnerabilities for which a patch was available but not applied—often for a year or more. This isn't about advanced threats; it's about unmanaged debt coming due. Your security program might be forward-focused on the latest threat intelligence, but if you're not actively managing this backlog, you're building your defenses on a foundation of known cracks.
What's on Your Security Debt Ledger?
Security debt isn't a single thing; it's a portfolio of neglected risks. To manage it, you first need to itemize it. Typically, it falls into four key categories:
Vulnerability & Patch Debt: The classic "known unknowns." This includes unpatched CVEs, outdated software libraries (like
log4j-type dependencies lingering in your codebase), and end-of-life systems no longer receiving vendor support. A tool like OWASP Dependency-Check (https://owasp.org/www-project-dependency-check) can automatically scan your projects for these vulnerable libraries.Configuration & Hygiene Debt: The "we did it for speed" compromises. Think default passwords unchanged, unnecessary network ports left open, cloud services (like AWS S3 buckets or Azure Blob Storage) configured as public, or excessive user permissions that were never revoked. OpenSCAP (https://www.open-scap.org/) provides robust, automated configuration baseline checking against established security standards.
Identity & Access Debt: The "who has access to what?" mess. This encompasses orphaned accounts from departed employees, privilege creep where users accumulate unnecessary rights, shared service accounts with no individual accountability, and a lack of Multi-Factor Authentication (MFA) on critical systems.
Architectural & Process Debt: The deepest and most costly debt. This is foundational: a flat network with no segmentation, missing encryption for data at rest, no formal incident response plan, or a lack of security training for developers. This debt often requires significant investment to remediate.
The Assessment Framework: Quantifying Your Risk, Not Just Your To-Do List
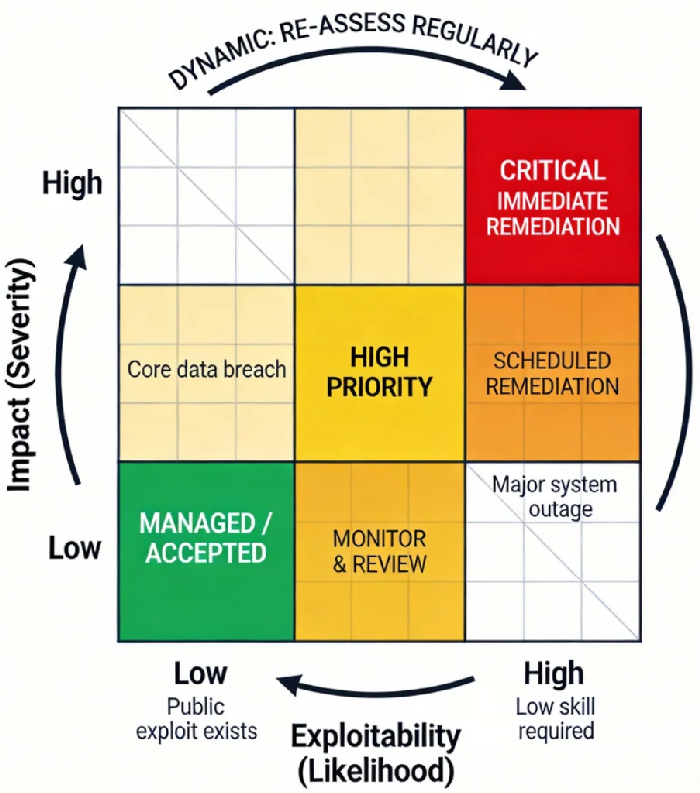
You can't fix what you can't measure, and you can't prioritize what you can't quantify. Throwing a giant list of vulnerabilities at a team is paralyzing. Instead, you need a framework to assess the actual risk of each debt item. I propose a simple but powerful Risk-Priority Matrix that evaluates each item on two axes:
Exploitability (Likelihood): How easy is it for this weakness to be used in an attack?
High: Public exploit code exists; system is internet-facing; attack requires low skill.
Medium: Exploit requires specific conditions or some internal access.
Low: Exploit is highly complex, theoretical, or requires physical access.
Impact (Severity): What is the business consequence if this is successfully exploited?
High: Compromise of core business data (PII, IP), financial systems, or critical infrastructure; major regulatory fines; severe reputational damage.
Medium: Disruption of non-critical services, limited data exposure, moderate recovery costs.
Low: Impact is contained to an isolated, low-value system.
Plotting your debt items on this matrix creates three clear action zones:
The "Critical" Quadrant (High Exploitability, High Impact): Immediate Remediation. This is your five-alarm fire. Allocate resources to fix these within days. Example: A public-facing web server with a critical Remote Code Execution (RCE) vulnerability.
The "High Priority" Quadrant (High/Likelihood + Medium/Impact or vice versa): Scheduled Remediation. Plan and execute fixes within the next sprint or monthly cycle. Example: An internal database with a high-severity flaw, but it's behind a firewall.
The "Managed/Accepted" Quadrant (Low Exploitability and/or Low Impact): Document and Monitor. Not all debt needs immediate repayment. Formally accept the risk (with business approval), document the rationale, and re-assess it quarterly. Example: An isolated, air-gapped legacy system running an old OS with no patch available.
The crucial insight here is that this assessment is not static. A debt item in the "Managed" zone can rocket into the "Critical" zone overnight if a new exploit is published. Your framework must be dynamic.
The Remediation Playbook: A Four-Phase Operational Plan
Assessment is pointless without action. Here is a phased, operational plan to move from overwhelmed to in-control.
Phase 1: Discovery & Inventory (Weeks 1-2)
Goal: Shine a light on the darkness. Create your initial Debt Ledger.
Actions:
Run comprehensive vulnerability scans (using tools like Nessus or OpenVAS).
Conduct automated configuration audits for cloud and on-prem assets.
Perform an identity and access review. Tools like BloodHound (https://github.com/BloodHoundAD/BloodHound) for Active Directory or cloud-native IAM analyzers can map terrifyingly expansive attack paths you never intended.
Output: A centralized list (a simple spreadsheet or a dedicated tool like Jira or ServiceNow) containing all identified debt items.
Phase 2: Triage & Prioritization (Week 3)
Goal: Apply your Risk-Priority Matrix. Stop debating what to do first.
Actions:
Assemble a "war room" with security, IT, and relevant business unit leads.
For each major debt item, collectively score its Exploitability and Impact. This business-context conversation is irreplaceable.
Assign each item to the Critical, High Priority, or Managed/Accepted zone.
Output: A prioritized, categorized Debt Ledger with clear owners and target dates for Critical/High items.
Phase 3: Execution & Validation (Ongoing)
Goal: Systematically pay down the highest-risk debt.
Actions:
Integrate "debt repayment" tasks into your standard sprint planning or IT change cycles. Treat them with the same rigor as new feature work.
Fix: Apply patches, tighten configurations, remove excess privileges.
Verify: Re-scan or manually test to confirm the fix is effective and hasn't broken anything.
Close & Document: Update the Debt Ledger. This log becomes invaluable for audits and demonstrates proactive risk management.
Pro Tip: Implement a "Security Iteration" – dedicate a specific sprint or a percentage of every sprint exclusively to reducing security debt.
Phase 4: Cultural Shift & Prevention (The Forever Phase)
Goal: Stop accumulating debt faster than you can pay it off.
Actions:
Shift Left: Integrate security scanning (SAST, SCA) directly into the CI/CD pipeline with tools like GitLab CI/CD or Jenkins with security plugins. Catch vulnerable libraries before they merge.
Automate Hygiene: Use Infrastructure as Code (IaC) tools like Terraform to define secure configurations by default. Use policy-as-code tools like Checkov or Terrascan to scan IaC templates for misconfigurations before deployment.
Establish Gates: Define hard security requirements for production. No system deploys with "Critical" or "High" debt items. Make debt visible on the business dashboard.
Managing security debt isn't about achieving a mythical state of "perfect security." It's about the disciplined, ongoing practice of cybersecurity hygiene. It's acknowledging that in the race to innovate, we will sometimes take on risk, but we must do so consciously, with our eyes open to the balance sheet.
The goal is to transform that background feeling of anxiety into a foreground process of control. When you have a clear ledger, a rational framework for prioritization, and an operational plan for remediation, security stops being a nebulous source of fear and "no's." It becomes a measurable, manageable engineering discipline.
Start today. Pick one system—just one. Scan it, list every known weakness, and place just the top item on that Risk-Priority Matrix. Then fix it. You'll have taken the first, most critical step: converting invisible, accruing risk into a visible, closed task. In the marathon of digital security, that's how you build endurance and ensure you're still running strong miles—and years—down the road.

